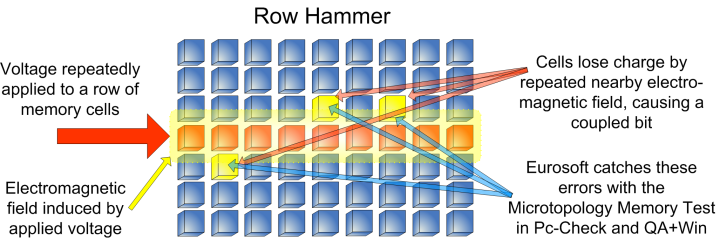
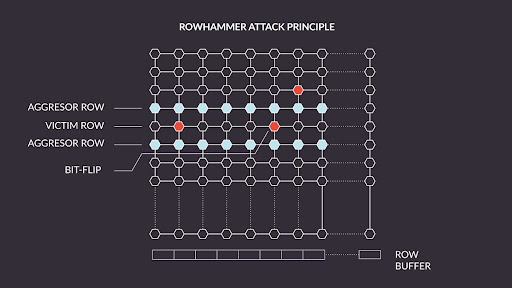
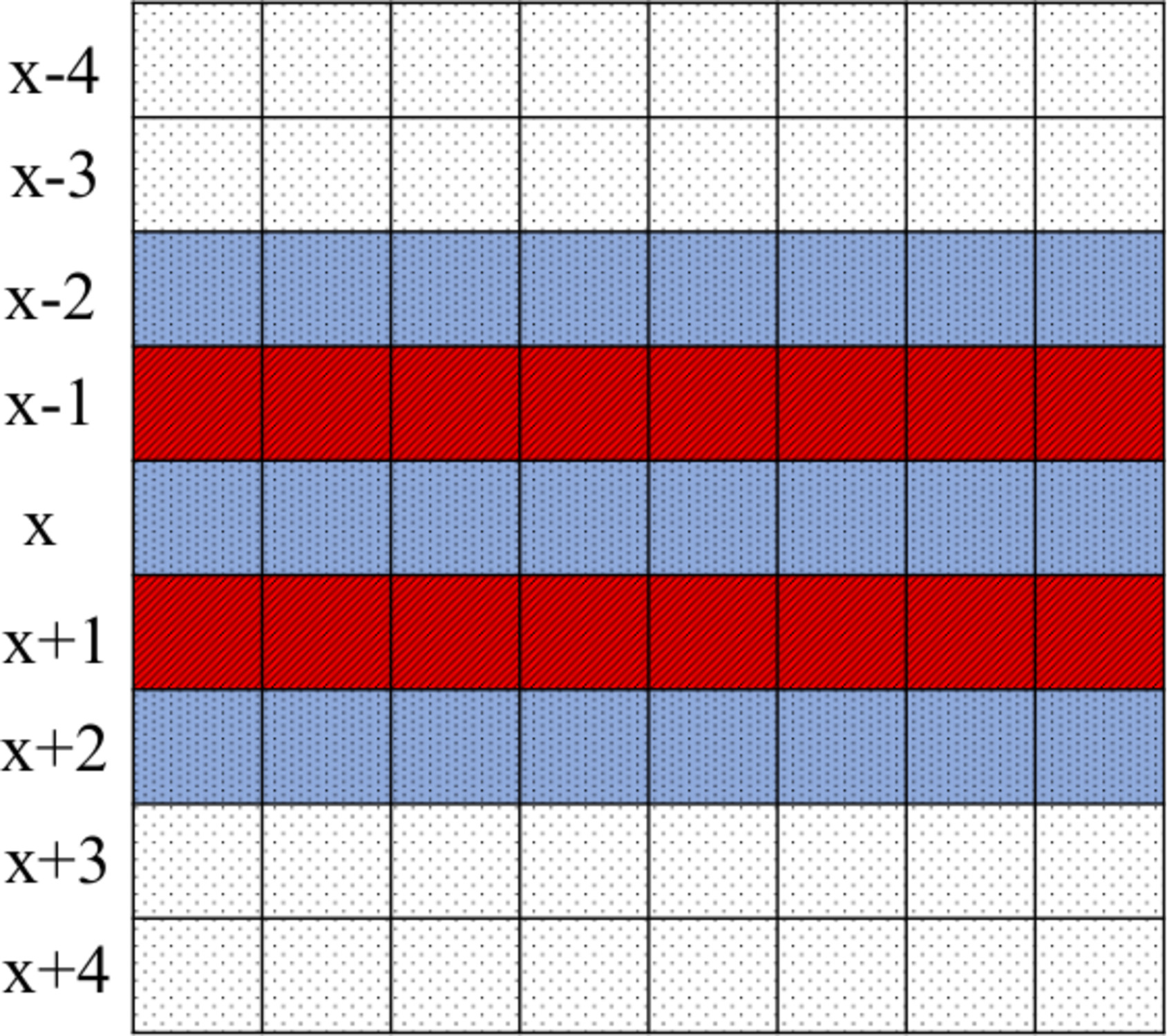
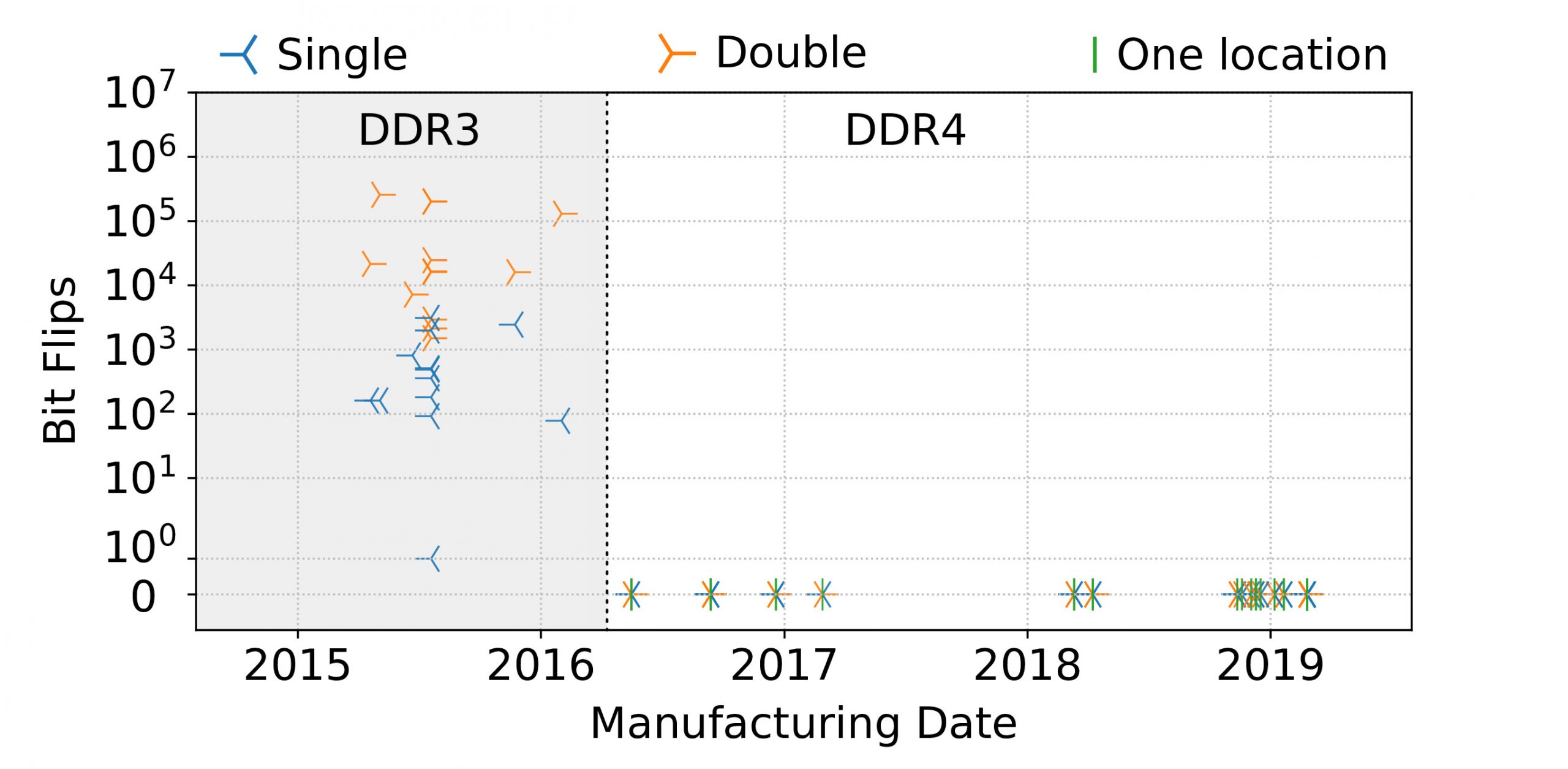
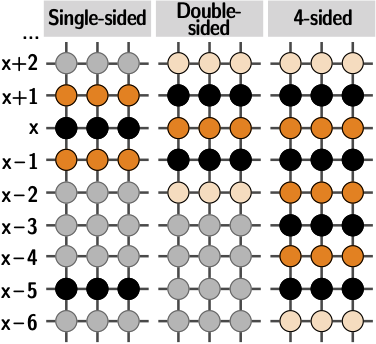
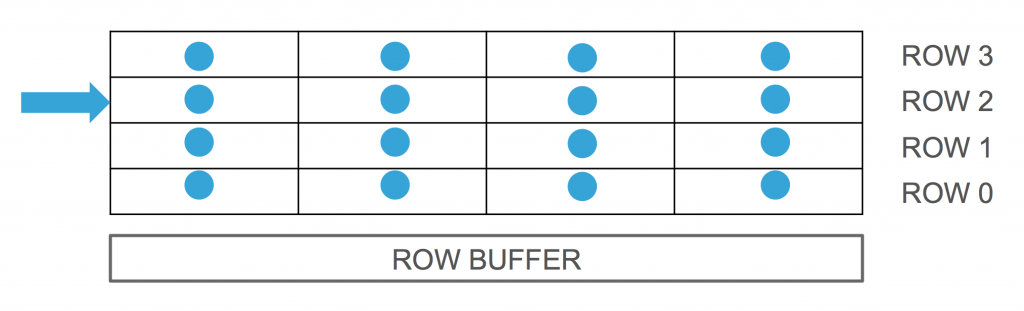
Google Online Security Blog: Introducing Half-Double: New hammering technique for DRAM Rowhammer bug
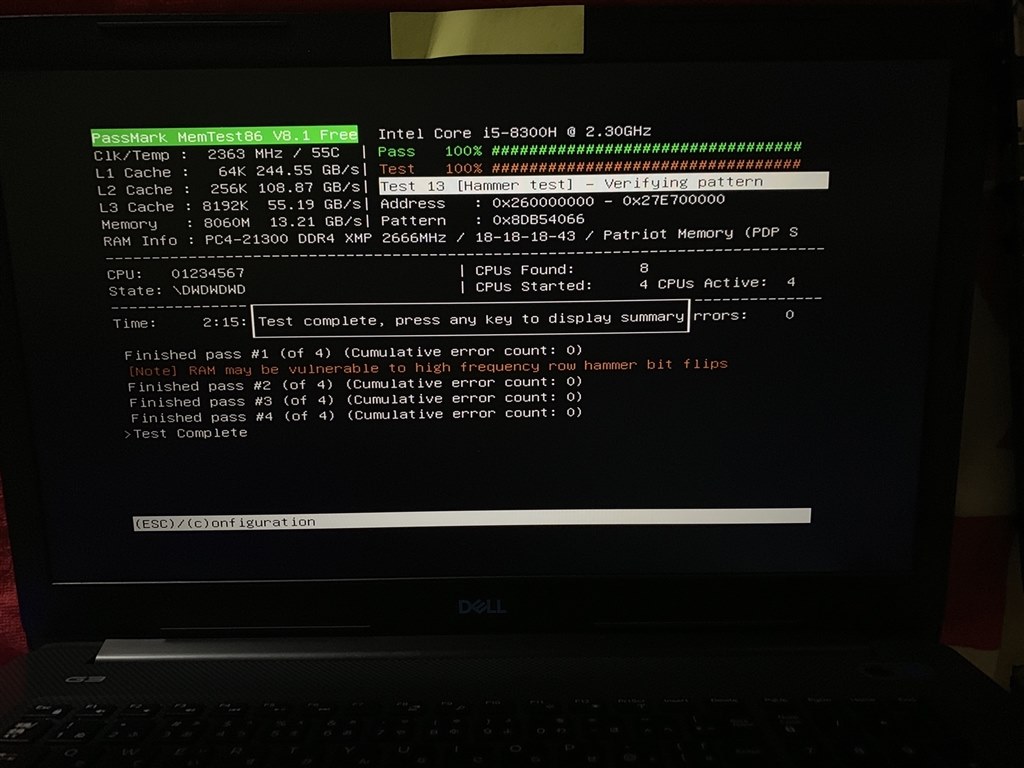
Introducing 'Blacksmith', a tool that can break through the security of almost all memory - GIGAZINE
How Rowhammer Weakness ow Rowhammer Could Be Used to Exploit Weaknesses in Computer Hardware Be Used to Exploit uter Hardware
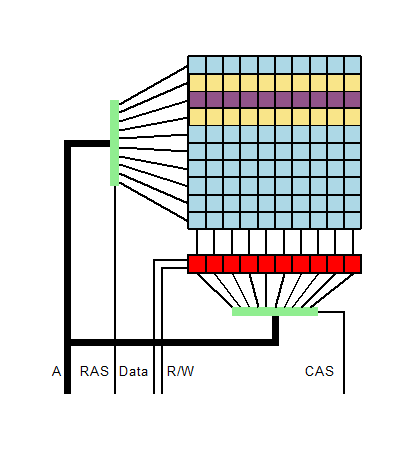
![Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium](https://miro.medium.com/max/1400/1*RiU39j2IHVBTFyXRewDEew.png)